Block IP Spammer on Postscreen Postfix with Fail2ban
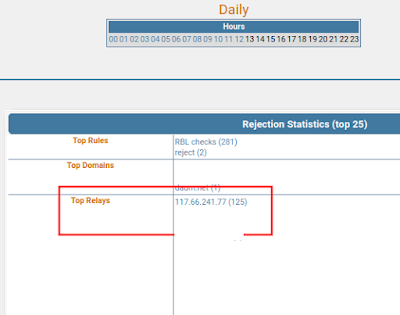
Karena ada ip selalu mencoba kirim spam, kita bisa mem block IP nya tersebut setelah beberapa kali ditolak karena ip reputasi nya tidak baik, ip tersebut tidak punya ciri legitimate mail server yang baik dan benar, parahnya lagi ip tersebut mencoba konek sebanyak 125 kali kurang dari 24 jam terakhir ke salah satu [email protected] dan potongan log nya sbb. dan pastikan fail2ban sudah berjalan normal
Mar 5 02:24:02 antispam postfix/postscreen[112526]: CONNECT from [117.66.xx.xx]:56802 to [10.10.0.31]:25
Mar 5 02:24:02 antispam postfix/dnsblog[112529]: addr 117.66.xx.xx listed by domain rbl.org as 127.0.0.2
Mar 5 02:24:02 antispam postfix/dnsblog[112533]: addr 117.66.xx.xx listed by domain rbl.org as 127.0.0.3
Mar 5 02:24:02 antispam postfix/dnsblog[112533]: addr 117.66.xx.xx listed by domain rbl.org as 127.0.0.4
Mar 5 02:24:02 antispam postfix/dnsblog[112533]: addr 117.66.xx.xx listed by domain rbl.org as 127.0.0.2
Mar 5 02:24:02 antispam postfix/dnsblog[112536]: addr 117.66.xx.xx listed by domain rbl.org as 127.0.0.2
Mar 5 02:24:02 antispam postfix/dnsblog[112528]: addr 117.66.xx.xx listed by domain b.rbl.org as 127.0.0.2
Mar 5 02:24:03 antispam postfix/dnsblog[112531]: addr 117.66.xx.xx listed by domain k.rbl.org as 127.0.0.2
Mar 5 02:24:14 antispam postfix/postscreen[112526]: DNSBL rank 28 for [117.66.xx.xx]:56802
Mar 5 02:24:15 antispam postfix/postscreen[112526]: NOQUEUE: reject: RCPT from [117.66.xx.xx]:56802: 550 5.7.1 Service unavailable; client [117.66.xx.xx] blocked using b.rbl.org; from=<[email protected]>, to=<[email protected]>, proto=ESMTP, helo=<domain.co.kr>
Mar 5 02:24:15 antispam postfix/postscreen[112526]: DISCONNECT [117.66.xx.xx]:56802
1. Buat filter fail2ban
di /etc/fail2ban/filter.d/postfix-rbl-postscreen.conf
[INCLUDES]
before = common.conf
[Definition]
_daemon = postfix/postscreen
failregex = ^%(__prefix_line)sNOQUEUE: reject: RCPT from \[<HOST>\]:.*550 5.7.1.* to=<[email protected]>.*$
ignoreregex =
# Author: Fals
2. Tambahkan jail
di /etc/fail2ban/jail.local
[postfix-rbl-postscreen]
enabled = true
logpath = /var/log/mail.log
filter = postfix-rbl-postscreen
action = iptables-multiports[name=postfix-rbl-postscreen, port="25,465,587", protocol=tcp]
maxretry = 16
bantime = 7d
findtime =48h
3. restart service fail2ban
Salam
Semoga Bermanfaat


Komentar
Posting Komentar